What is OpenSCAP?
Security Content Automation Protocol (SCAP)
SCAP is a standardized compliance checking solution for enterprise-level Linux infrastructure. It is a line of specifications maintained by the National Institute of Standards and Technology (NIST) for maintaining system security for enterprise systems.
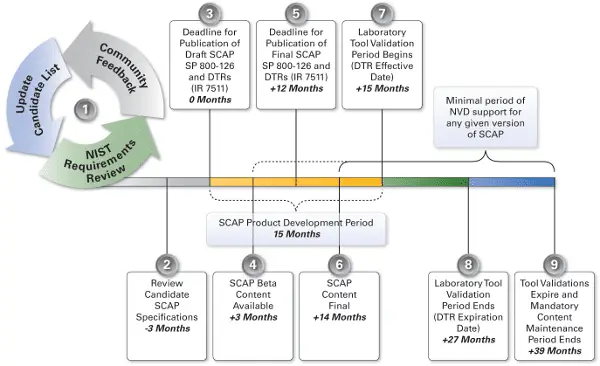
To guard against security threats, organizations need to continuously monitor the computer systems and applications they have deployed, incorporate security upgrades to software and deploy updates to configurations. The Security Content Automation Protocol (SCAP), pronounced “ess-cap”, comprises a number of open standards that are widely used to enumerate software flaws and configuration issues related to security. Applications which conduct security monitoring use the standards when measuring systems to find vulnerabilities, and offer methods to score those findings in order to evaluate the possible impact. The SCAP suite of specifications standardize the nomenclature and formats used by these automated vulnerability management, measurement, and policy compliance products.
A vendor of a computer system configuration scanner can get their product validated against SCAP, demonstrating that it will interoperate with other scanners and express the scan results in a standardized way.
SCAP Components
SCAP standard family comprises of multiple component standard. The components are designed to work together the common goal. For each component the standard defines a document format with syntax and semantics of the internal data structures. All the component standards are based on Extensible Markup Language (XML) and each component standard defines its own XML namespace. Different versions of the same component standard (language) may also be distinguished by different XML namespace.
SCAP standard consists of these components: XCCDF, OVAL, DataStream, ARF, CPE, CVE, CWE.
Some features implemented OpenSCAP are not covered by SCAP standards specification although they are interoperable with SCAP — e.g. Script Check Engine. For these we try to release the specification to allow interoperability with other vendors.
XCCDF
The XCCDF acronym stands for Extensible Configuration Checklist Description Format. As the name suggests, the language is used to describe the security checklists. The language is designed to support information interchange, document generation, organizational and situational tailoring, automated compliance testing, and compliance scoring.
OVAL
The OVAL acronym stands for Open Vulnerability and Assessment Language. OVAL is declarative language for making logical assertions about the state of system. It is main component of the SCAP standard. It is used to describe security vulnerabilities or desired configuration of systems. OVAL definitions define a secure state of some objects in a computer, for example configuration files, file permissions, processes. OVAL definitions are evaluated using an interpreter called scanner.
DataStream
DataStream is a format that packs other SCAP components into a single file. This is useful when distributing SCAP content for example over WWW, because a single file is easier to handle.
ARF
The Asset Reporting Format (ARF) consolidates multiple result files (OVAL results and XCCDF results). It is also often called Result DataStream.
CPE
The Common Platform Enumeration (CPE) serves to identify IT platforms and systems using unequivocally defined names. CPE also includes a method for checking names against a system, and a description format for binding text and tests to a name.
CVE
Common Vulnerabilities and Exposures (CVE) is a reference dictionary for publicly known security vulnerabilities and exposures. CVE provides standardized names (identifiers) of vulnerabilities. The CVE allows interoperability between different security tools.
CWE
Common Weakness Enumeration (CWE) is a community-developed list of software weaknesses. CWE leads its effort to describe in detail known security weaknesses and flaws. It also provides information about prevention, implementation and mitigation of a weakness. The project is supported by the MITRE Corporation. For more information, please visit CWE website.
SCE
The Script Check Engine: SCAP extension to allow script execution from SCAP policy. It allows you to make your scripts interoperable with your security policy. For more information, please visit SCE page.
Other Standard Componenets
The security compliance space is very diverse. There are many standards, specifications and recommendations out there. Some of them are designed to be used with SCAP and we do our best to support those use-cases. Some are orthogonal and may even be designed to replace SCAP at some point.
We are pro-actively discovering new standards and are evaluating possibilities to extend OpenSCAP to be inter-operable with them.
SACM
Security Automation and Continuous Monitoring is a life-cycle process which provides effective asset control and efficient delivery of information. The process includes managing resources (infrastructure, data), capabilities (people) and artifacts (HWs, SWs, Documentation).
As of September 2015 SACM is a standard proposed via an IETF working group. The specification documents are in draft state.
SWID
Software identification tags (SWID tags) record unique information about an installed software application, including its name, edition, version, whether it’s part of a bundle and more. It’s an XML file that’s installed alongside software, and which uniquely identifies the software, providing data for software inventory and asset management.
While SWID is not widely used yet it may have a promising future as its adoption ramps up.
CC
Common Criteria is an international standard for certifying computer security software. Using Protection Profiles, computer systems can be secured to certain levels that meet requirements laid out by the Common Criteria.
FIPS
The Federal Information Processing Standards is official set of standards developed by the United States federal government. They apply to use of computer systems by non-military government agencies, government contractors and vendors who work with the agencies. These standards are issued to establish requirements for various purposes such as ensuring computer security and interoperability, and are intended for cases in which suitable industry standards do not already exist.
For more information, please visit the FIPS website at NIST.
What is OpenSCAP?
OpenSCAP is an auditing tool that utilizes the Extensible Configuration Checklist Description Format (XCCDF). XCCDF is a standard way of expressing checklist content and defines security checklists. It also combines with other specifications such as CPE, CCE, and OVAL, to create a SCAP-expressed checklist that can be processed by SCAP-validated products.
OpenSCAP Features
OpenSCAP main features are as follows:
Security Compliance
In order to minimize the threat of an attack on computer infrastructure, or even completely prevent it, many institutions in both the private and public sectors have adopted the concept of enforcing a security policy or a security benchmark. These policies define security requirements which all systems used by the institution must meet. It applies not only to systems physically located within the organizations, but often to any third party environments have access to the organizations’ computer infrastructures. In some cases, these policies are defined by government regulations, but many businesses adopt their own security policies even if they are not specifically required to do so by law.
Vulnerability Assessment
Any organization wishing to protect itself against these attacks must set up a proper and sustainable vulnerability management policy. A good policy satisfies multiple key concepts, which include:
- Detailed knowledge of the underlying computer infrastructure
- Continuous delivery of certified information about currently known security flaws and their impact
- Quick identification of the current security status of each system (security analysis)
- Prompt reaction — capability to instantly perform corrective operations where necessary (remedial action)
- Possibility to perform security analysis in automated,unattended way on regular basis, regardless of the infrastructure’s complexity
- Availability of proper software tools to carry out these tasks with minimal effort while preventing or at least minimizing outage periods
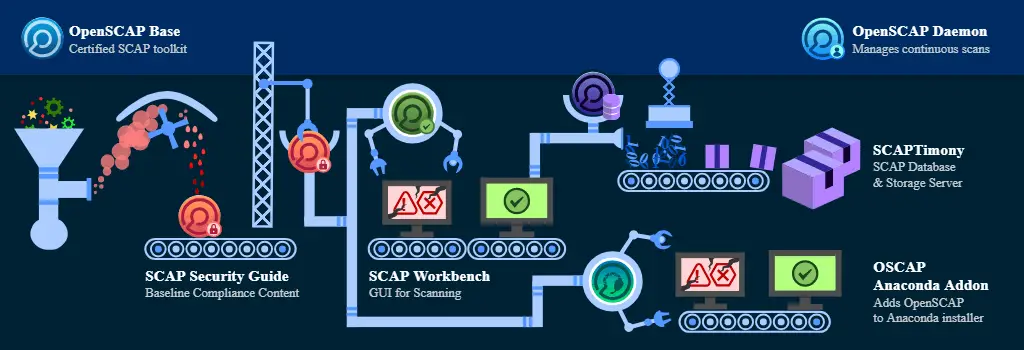
OpenSCAP Tools
- OpenSCAP Base: With the oscap tool you can perform configuration and vulnerability scans, validate your SCAP content in line with SCAP standard XML schemas, display basic information about your content, or list profiles in an XCCDF benchmark. It’s available for Windows and Linux.
-
OpenSCAP Daemon: The OpenSCAP Daemon is a service that runs in the background. It makes sure your machines and containers are evaluated according to the schedule you specify. Functionality can be divided into two categories continuously evaluating machines against a specific policy, and one-off evaluation.
-
SCAP Workbench: That is a graphical utility that offers an easy way to perform common oscap tasks. This tool allows users to perform configuration and vulnerability scans on a single local or a remote system, perform remediation of the system in accordance with the given XCCDF or SDS file. Workbench can generate reports, in multiple formats, containing the results of a system scan. Workbench allows you to modify an XCCDF profile in an easy way without changing the respective XCCDF file. The tool provides a graphical way to enable or disable XCCDF elements. Your changes can be stored as an XCCDF tailoring file. SCAP Workbench is available for Linux and Windows.
-
SCAPtimony is middleware that stores SCAP results for your infrastructure and then allows the stored data to be manipulated. SCAPtimony is a SCAP storage and database server built on top of the OpenSCAP library. It can be deployed as a part of your Rails application (i.e. Foreman) or as a stand-alone sealed server. The SCAPtimony project gives full testimony about the compliance of your infrastructure. This is achieved by parsing all the SCAP results and storing important pieces in a database. SCAPtimony also provides the ability to perform common database queries on such data.
- OSCAP Anaconda Add-on:
Each time an operating system is installed it needs to be configured – but before the new settings are in place, there is a short period when the system is not configured in line with your policies. In many cases this is not a problem, however in a highly secured environment a misconfigured system poses a threat. OSCAP-Anaconda-Addon solves this exact problem. It is an add-on for the Anaconda installer that enables administrators to feed security policy into the installation process and ensure that systems are compliant from the very first boot. The easiest way to use OSCAP-Anaconda-Addon is to pick a Linux distribution which comes with it built-in. Today, the only such distribution is Red Hat
The OSCAP Anaconda Addon supports the following modes of Anaconda installer operation:
- Graphical User Interface (GUI) mode,
- Kickstart file mode (using GUI or text mode)
OpenSCAP Security Guide
SCAP Security Guide is a security policy written in a form of SCAP documents. The security policy created in SCAP Security Guide covers many areas of computer security and provides the best-practice solutions. The guide consists of rules with very detailed description and also includes proven remediation scripts, optimized for target systems. SCAP Security Guide, together with OpenSCAP tools, can be used for auditing your system in an automated way.
SCAP Security Guide implements security guidances recommended by respected authorities, namely PCI DSS, STIG, and USGCB. SCAP Security Guide transforms these security guidance into a machine readable format which then can be used by OpenSCAP to audit your system. SCAP Security Guide builds multiple security baselines from a single high-quality SCAP content. The DISA STIG for RHEL 6, which provides required settings for US Department of Defense systems, is one example of a baseline created from this guidance. If your systems must to comply to these baselines, you simply select appropriate profile from SCAP Security Guide.
Security policies in SCAP Security Guide are available for various operating systems and other software – Fedora, Red Hat Enterprise Linux, Mozilla Firefox and others.
SCAP Security guide is a dynamic open source project, which means that many organizations interested in computer security share their efforts and collaborate on security policies contained in SCAP Security guide. It has usage in Military and Intelligence communities, healthcare, aviation, telecom and other industries. And above all, SCAP Security guide is available for download free.
Acronyms
AI
Asset Identification, part of the SCAP standard, is a language that provides a data model for identifying assets, methods for identifying assets, and guidance on how to use asset identification.
ARF
The Asset Reporting Format, part of the SCAP standard, is a language that expresses the transport format of information about assets, and the relationships between assets and reports. It is also often called Result DataStream because it is complementary to Source DataStream.
CCE
Common Configuration Enumeration, part of the SCAP standard, is an enumeration of security relevant configuration elements for applications and operation systems.
CCSS
The Common Configuration Scoring System, part of the SCAP standard, is a specification for measuring the relative severity of system security configuration issues.
CIS
The Center for Internet Security, Inc. (CIS) is a 501c3 nonprofit organization focused on enhancing the cybersecurity readiness and response of public and private sector entities.
CPE
Common Platform Enumeration, part of the SCAP standard, is a structured naming scheme used to identify information technology systems, platforms, and packages.
CVE
Common Vulnerabilities and Exposures, part of the SCAP standard, is an enumeration for publicly known information security vulnerabilities.
CVSS
The Common Vulnerability Scoring System, part of the SCAP standard, is a language for representing system configuration information, assessing machine state, and reporting assessment results.
CWE
Common Weakness Enumeration is a community project whose main task is to collect a catalog of software weaknesses and vulnerabilities and deal with them.
FIPS
The Federal Information Processing Standards are an official set of standards developed by the United States federal government. These standards describe document processing, encryption algorithms and more. They apply to the use of computer systems by non-military government agencies, government contractors and vendors who work with the agencies.
MITRE
MITRE is an American nonprofit Corporation which performs research & analysis, development, engineering and integration. They are sponsored by the federal government and have various research programs.
NIST
The National Institute of Standards and Technology is a federal technology agency. They advance official technology, measurement science and standards.
NVD
The National Vulnerability Database is the U.S. government repository of vulnerability management data, which enables automation of vulnerability management, security measurement, and compliance. NVD includes databases of security checklists, security related software flaws, misconfigurations, product names, and impact metrics.
OCIL
The Open Checklist Interactive Language, part of the SCAP standard, is a language for representing checks that collect information from people or from existing data stores made by other data collection efforts.
OVAL
The Open Vulnerability and Assessment Language, part of the SCAP standard, is declarative language for making logical assertions about the state of endpoint system.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) provides a baseline of technical and operational requirements designed to protect cardholder data. PCI DSS applies to all entities involved in payment card processing on one hand, and simultaneously to all subjects processing, transmitting, or storing cardholder data or sensitive user authentication information on the other.
See Also
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 1
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 2
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 3
[Download]: Critical HPE Servers ROM Update – Spectre Vulnerability