Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 3
Part 3, Resolving Security Issues
At the first part, we’ve reviewed GSM (Greenbone Security Manager – Formerly OpenVAS) as a security manager or assessment tool for discovering vulnerabilities on virtual environments, the second part was more functional and we talked more about GSM. You leaned that how can you create a target on Greenboone Security Manager and scan it to discover vulnerabilities.
As I said at the end of second part of the blog post, the third part is related to resolving security issues. Any software and specially operating systems have “Hardening Guide”. You must follow steps of hardening guide to reduce security vulnerabilities effect on production environments.
One step is same on all vendors hardening guides: Pleas install the latest patches.
So we’ll install latest patch on our ESXi server first.
Installing Security Patch
Fortunately, VMware releasing patches as cumulative which last patch covering all issues that released by older patches as well. So keep update ESXi server always by installing latest patches.
I don’t want to learn you that how should you upgrade components of virtual infrastructure, it’s just an example.
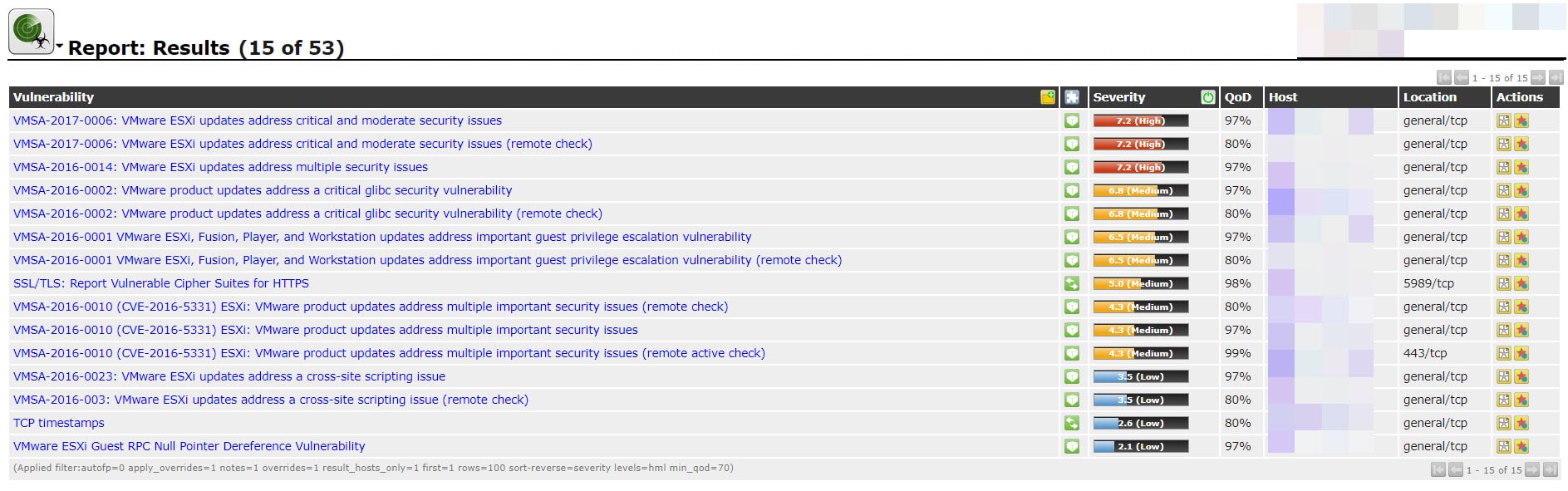
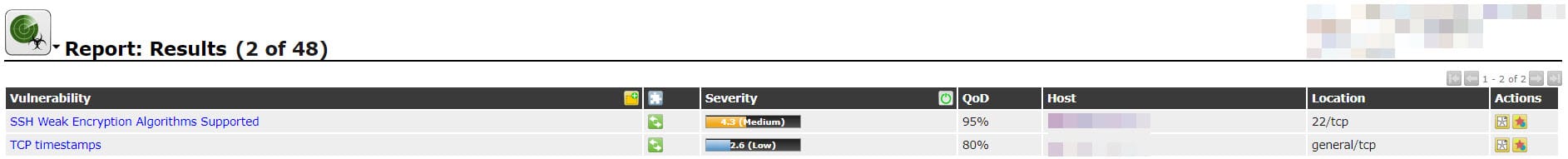
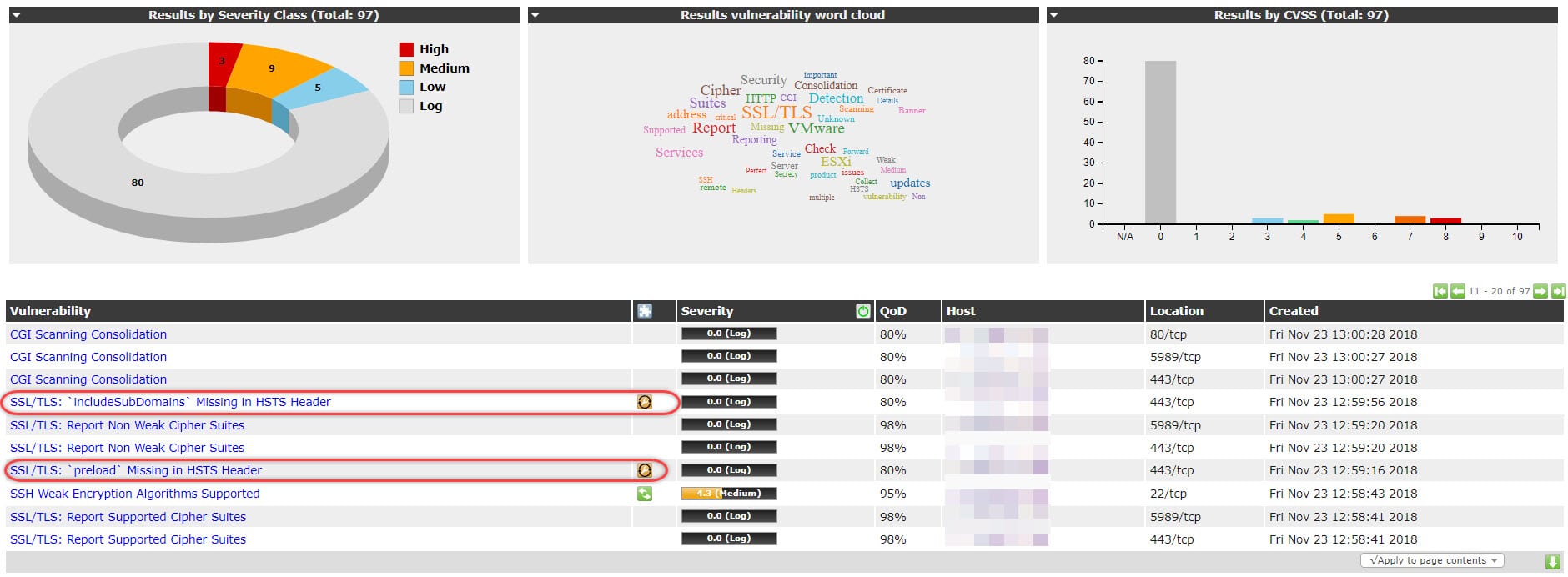
Anyway, here is the last scan result:
There was some high and medium security issues. Let’s install newest patch and scan the server again.
Yo know that there is some ways to installing ESXi patches such as Update Manager, CLI and others. Again, I don’t want to review patch installation or upgrade considerations. So you can install ESXi patch as you wish.
You can upload the patch file which it’s ZIP file on ESXi server datastore and run the below command as typical installation way:
esxcli software vib install -d /zip_file_path
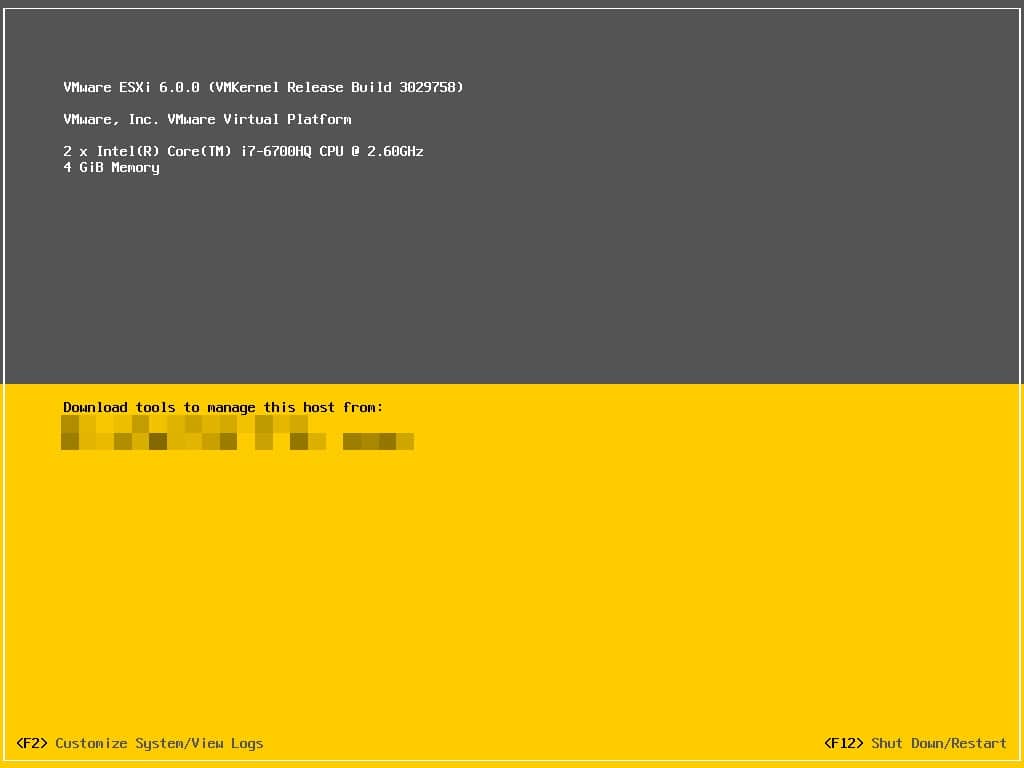
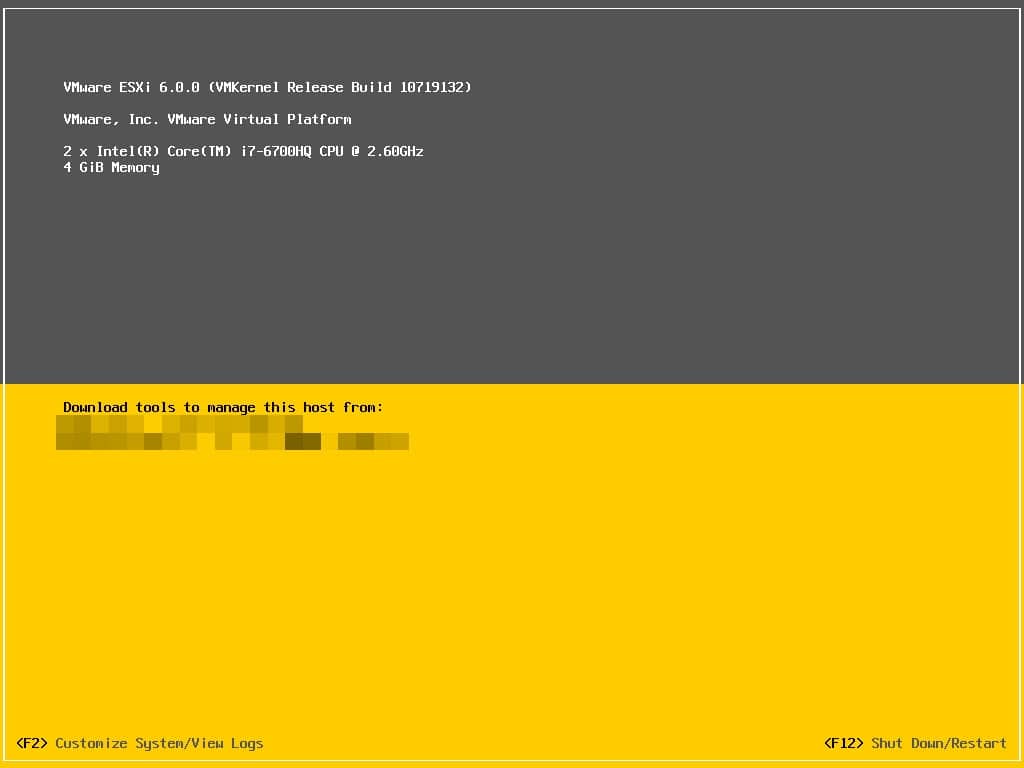
After installation, server should be rebooted. After boot-up, check ESXi build number.
That was simple example for applying patch on a server. In production environment, test new patches on test servers before applying on all production servers also if you have to apply patch or update multiple components such as ESXi and vCenter, check their compatibility before applying patches or upgrade.
Vulnerability Scan After Patch Installation
After installing patch, run the create task (Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 2) on GSM again.
After some minutes, the task will be finished and then you can compare result of task before and after patching.
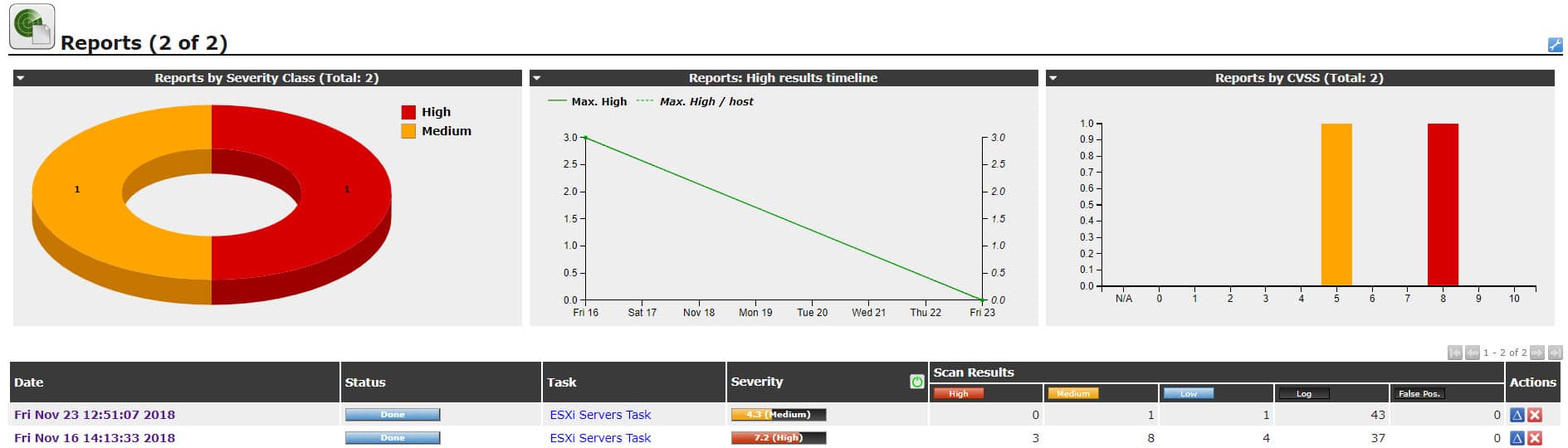
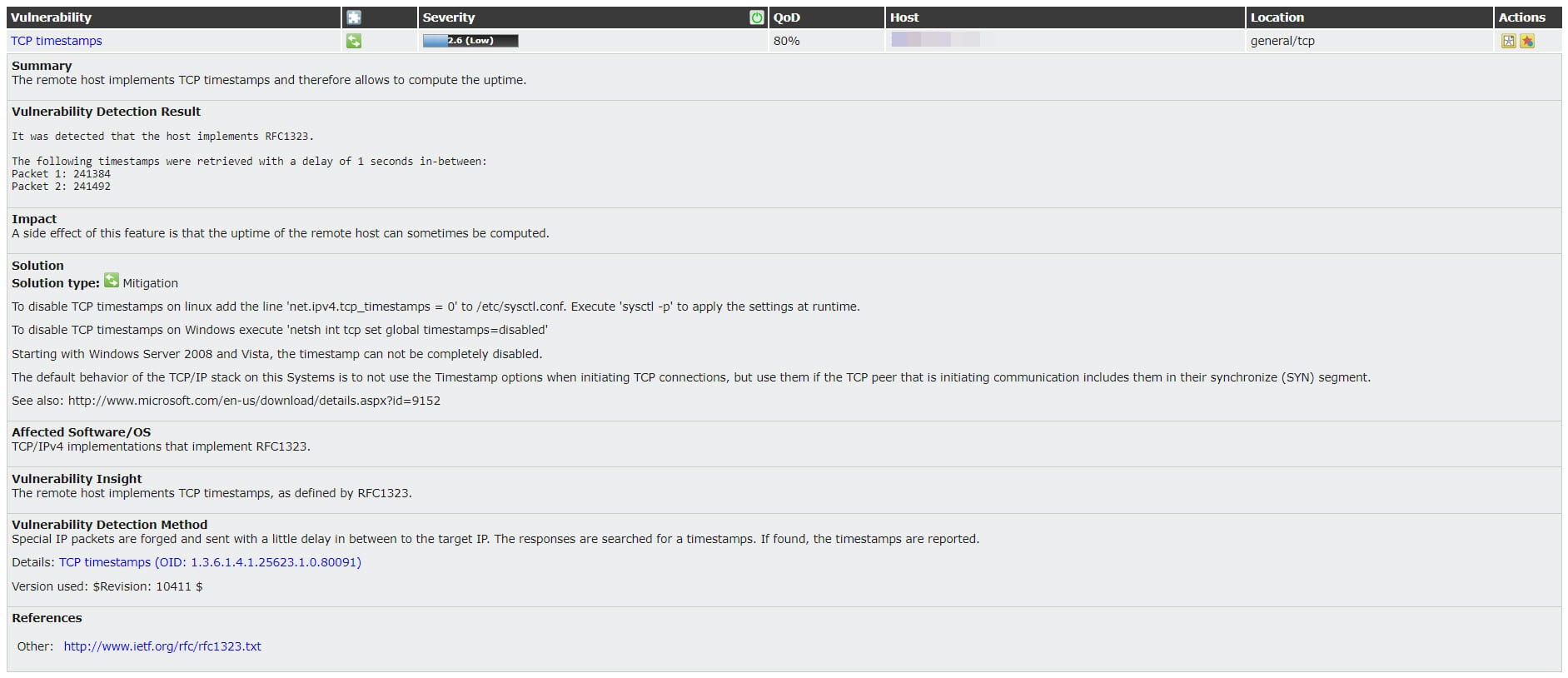
Summary of report shows that there is no high score vulnerability after patch installation, also medium and low vulnerability have been reduced to one. There is more logs and actually, logs are logs but check them as well.
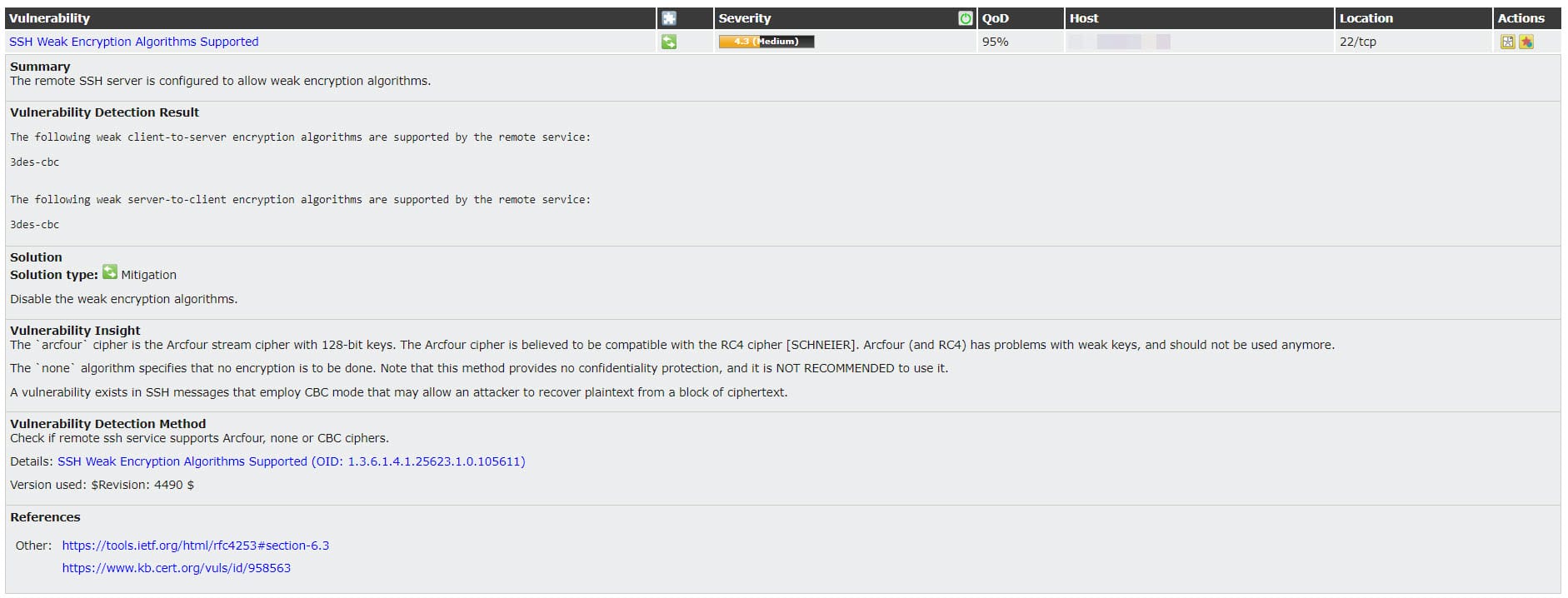
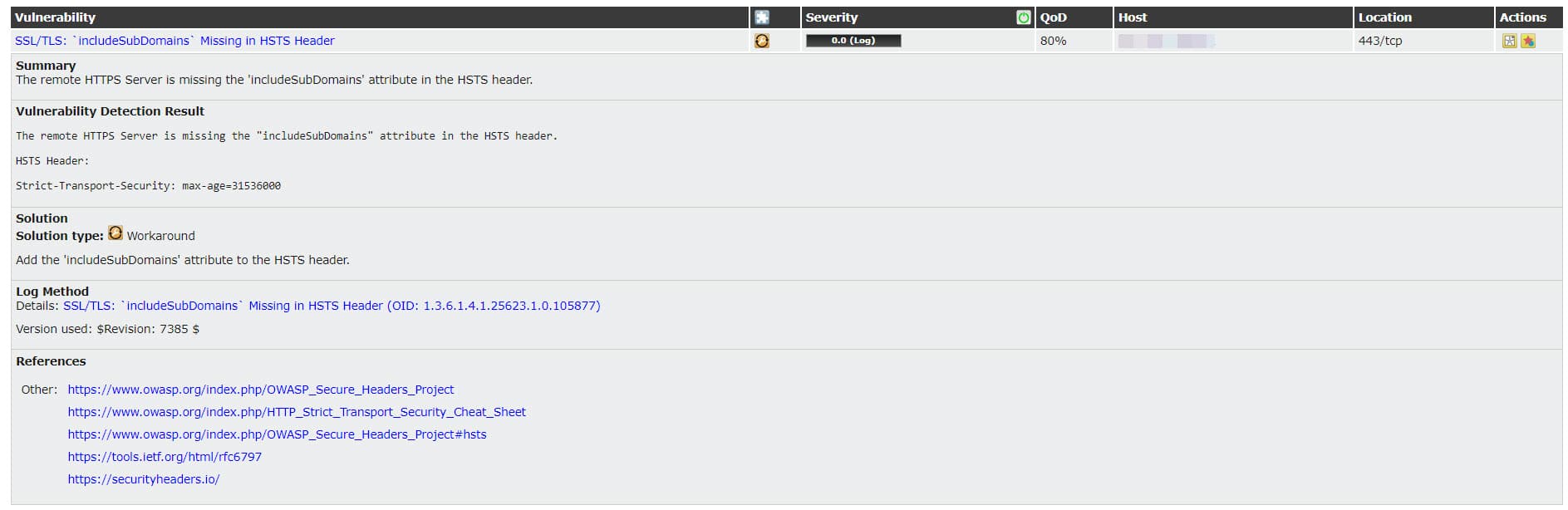
Actually, the vendor (VMware) has no patch for the discovered vulnerability and there is offered some mitigation for resolving those security issue. Please consider these mitigation to have safest environment. You can see the mitigation procedure and some helpful links by click on each vulnerability.
Now, host severity is medium. So if you were with me, we’ve scanned a host at the second part of “Virtual Environments Vulnerability Assessment By GSM” and we found that the server has sinuously security issues. Severity was high before patch installation. Then latest patch has been installed on that and now most of security issues are gone. Please keep in mind that security is relative, so this process should be repeated constantly to keep environment safe.
In addition of vendor patch and mitigation, there is some issues which be logged by GSM and offers you a workaround. Same as the above issues, you can find workaround by click on each log. Applying workarounds helping you to preventing any further security issue on server. Also there is some logs with no mitigation and no workaround, you can resolve it by follow producers but I recommend that test the procedure on test environment before applying on production also may be, there were just logs and there is no procedure but take a look tot those logs.
You can find logs on each task results. The logs will be increased after each time run.
Is It Finished?
Is it finished? I should say no, I said before that you must do it periodically but scanning and patching security issue are not all actions that you should do. Any software and operating system has hardening guide, so harden procedure should be applied on each server manually, automatically or by a configurations manager.
You can find VMware Hardening Guide on the below link:
https://www.vmware.com/security/hardening-guides.html
You’ll find hardening guide of your hypervisor and other software on vendor web site.
I hope that you found the blog post useful and it helps you to keep your virtual environment safe more than before. If you are using ESXi or other hypervisor on your environment, follow the blog post, scan and resolve security issues. Don’t forget that keep all virtual environment’s components safe and run scan on other components as well.
See Also
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 1
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 2











Thanks. All three posts are amazing.
I found them really useful. I learnt something new. In fact I was searching for similar tool. I tried but could not find your whether this tool is opensource or commerical.
Thank you for feedback. There is a community edition:
https://www.greenbone.net/en/community-edition/
Very informative article … I want to perform a vulnerability assessment of my company. Do you have any recommendations for tools, methodologies, etc, to suggest to me?
Hi,
Thanks for comment. I think, you have two options:
Pay for enterprise solutions such as Nexpose.
Use open-source solutions with some limitations.
I recommend that keep your servers hardened and apply latest patches on any software that you are using in company.
Also I think this is good article about methodologies:
https://cybersecurity.att.com/blogs/security-essentials/vulnerability-assessment-explained