Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 2
Scan ESXi Server By GSM (OpenVAS)
We have reviewed reasons of have Vulnerability Assessment or Vulnerability Manager in virtual environments and how these software help us to find vulnerabilities on any component of virtual infrastructure. We have reviewed OpenVAS or Greenbone Security Manager and talked about features and abilities at part 1.
Now, it’s time to use the GSM server that we had prepared on the previous part. In this part of blog post, we’ll configure a target (ESXi Server) on OpenVAS server, create a task for scan and find the result of scan.
I’ve installed ESXi 6U1 (3029758) on a virtual machine and there is no customized configuration, all configurations are default.
I recommend that if you have multiple hosts in production environment, choose one of hosts which have same security configurations for scan. If there is no issue for scanning whole virtual infrastructure, you can do it but you’ll waste time for mitigation because based on my experiences, you did same configuration on your hosts with same version and build number!
Now and at the first step, logon to GSM server web interface:
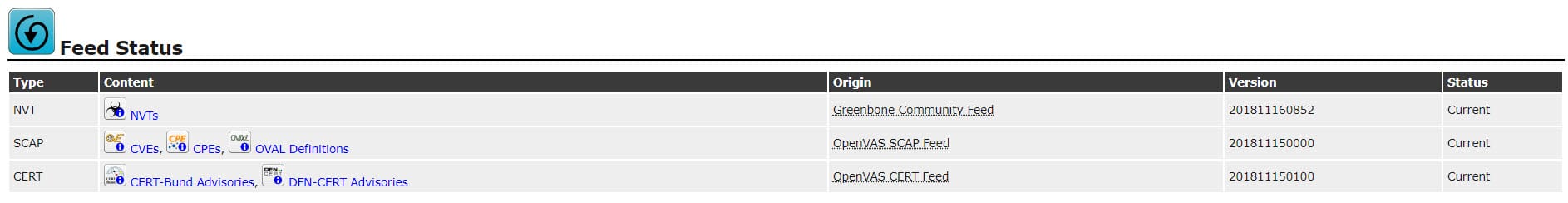
Checking Feed Status
Before start to any other action on GSM, Feed Status should be checked. Scanning servers with outdated feeds will a mistake. Check feed status via the below menu:
Extra -> Feed Status
All feeds status should be show as “Current”, it means that feeds are updated automatically or manually. Otherwise do feed update via server console.
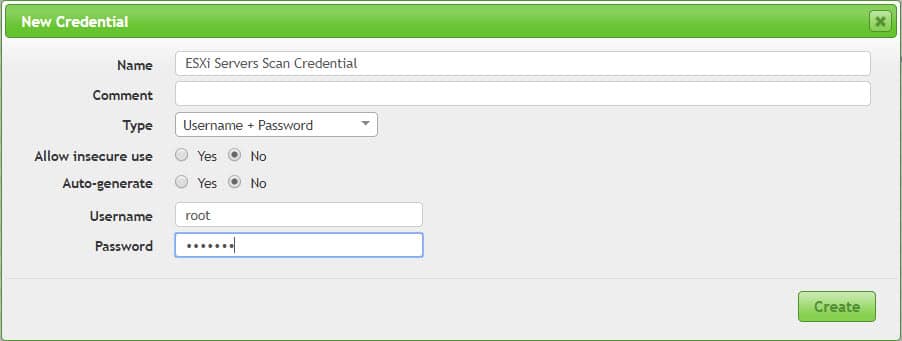
Define Credential
In order to have accurate scan results, you need to allow GSM to logon and check vulnerabilities within Hypervisor. you can define four types of credentials via the below menu:
Configuration -> Credentials
I have used “root” user for Credential creation but it doesn’t recommend.
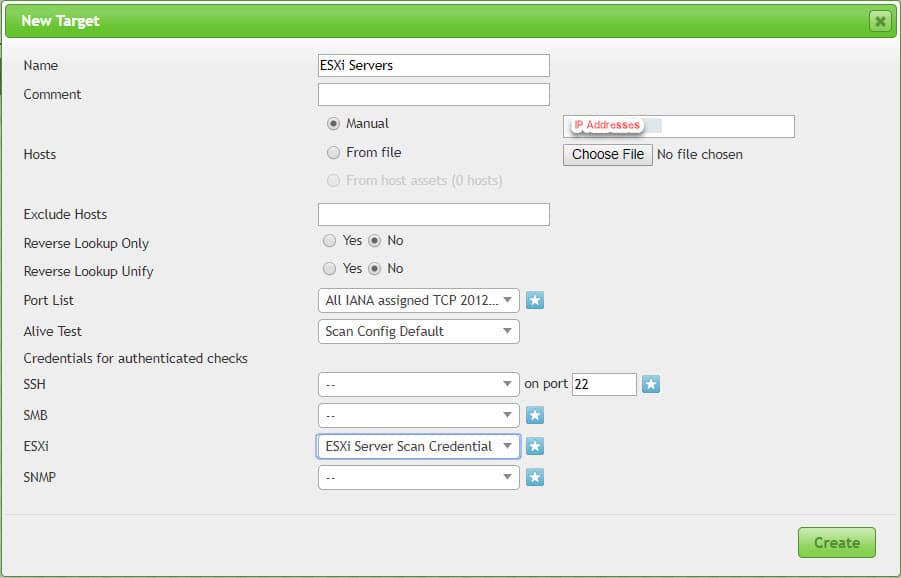
Define Target
Before start to any scan, you need to define target that will be used in Scan tasks. The target can be a device or range of addresses for devices or current hosts. For the test, I’ve choose defined credential and left other configurations same as default.
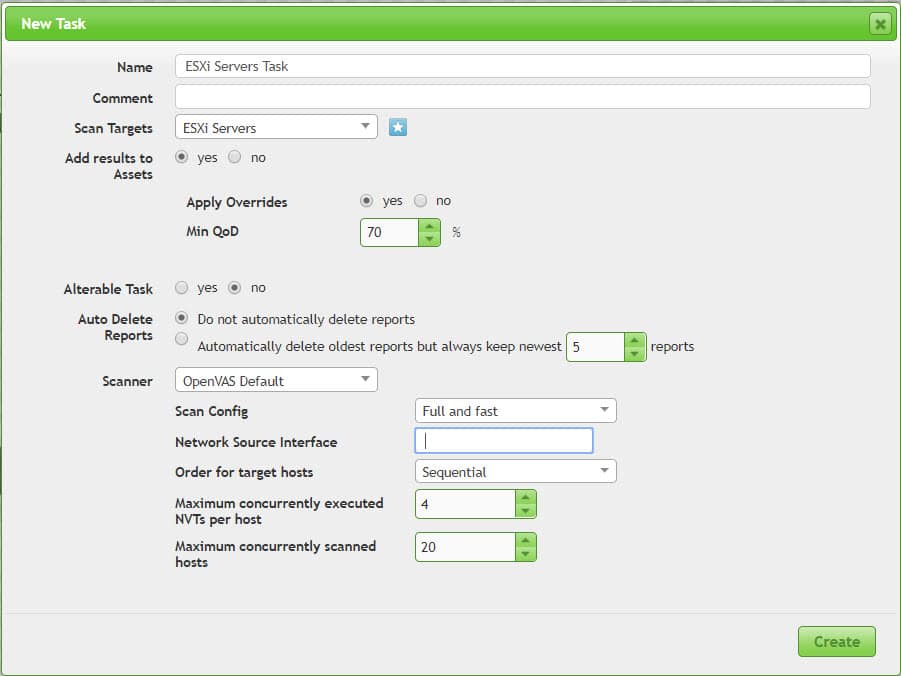
Define Scan Task
Scan tasks can be defined for scanning targets, after defining a task, it should be run manually. You can run a task ultimately, GSM can keep some or all reports for each run. You can compare results of tasks and compare discovered security issues. Reports are exportable, so you can export it to different document types such as PDF for offline review.
Scan tasks should be defined via the below menu:
Scan -> Tasks
You can use customized tasks. I’ve used default configuration for this test.
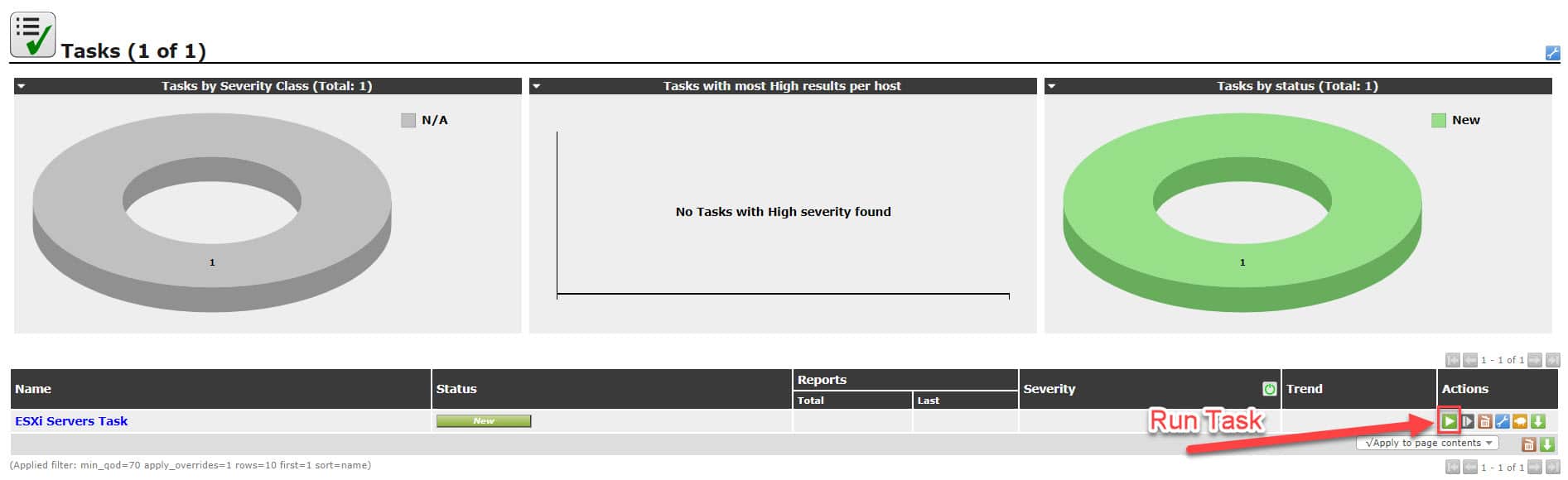
After defining any task, It will be show in “New” status and should run manually.
After run the task, its state will be changed to running and you can monitor discovered issues by click on task name but discovering issues may be take some minutes.
By click on any item in vulnerability column, you will see details of that and workarounds or mitigation.
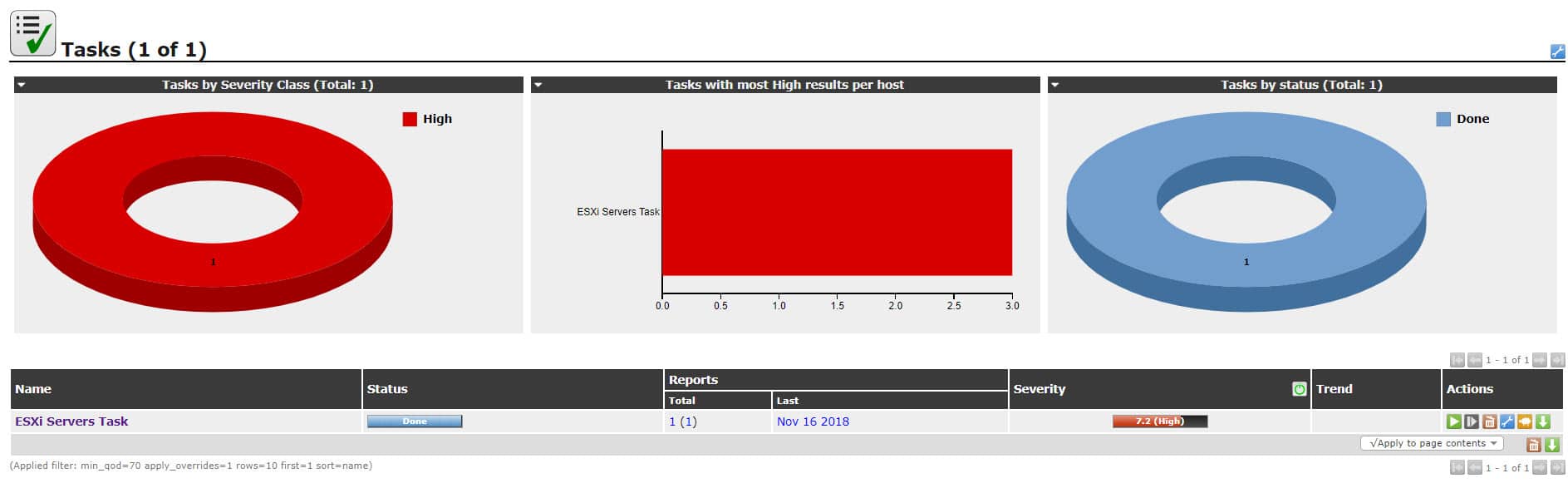
When scan is finished, target will be categorized by Severity. Because I used old version of ESXi 6.x, GSM discovers many security issues and warn me that the server is at high risk state.
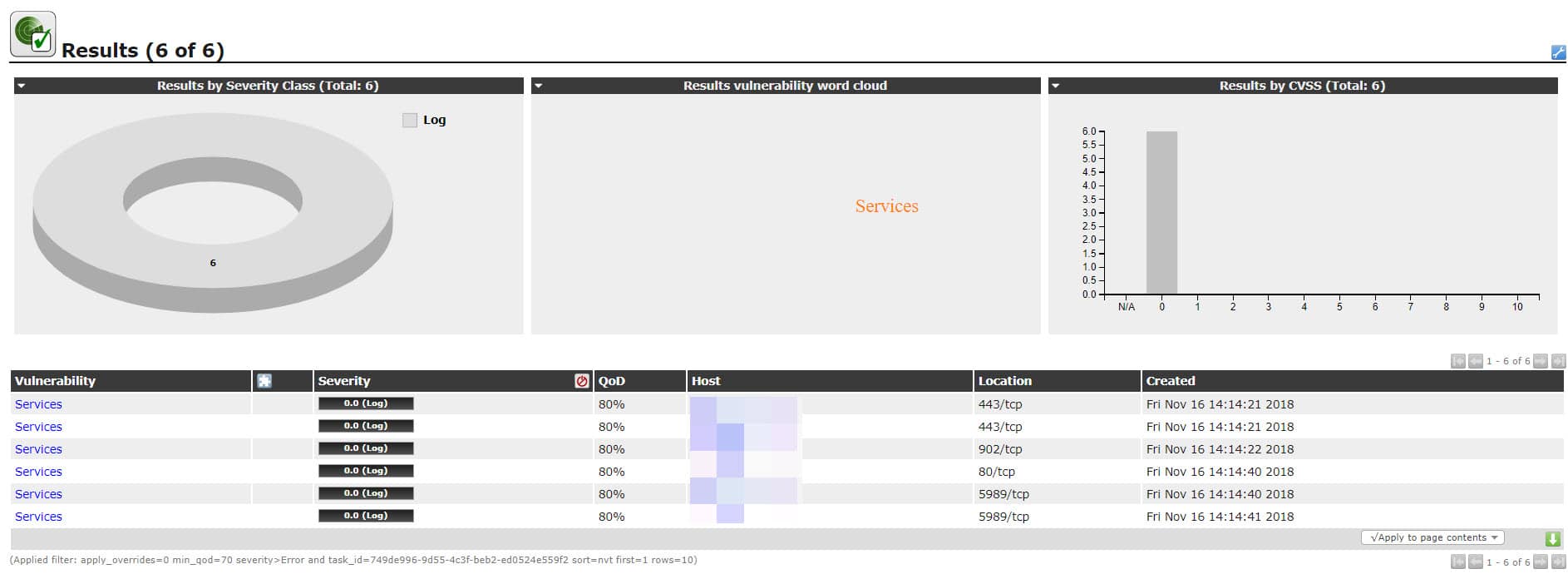
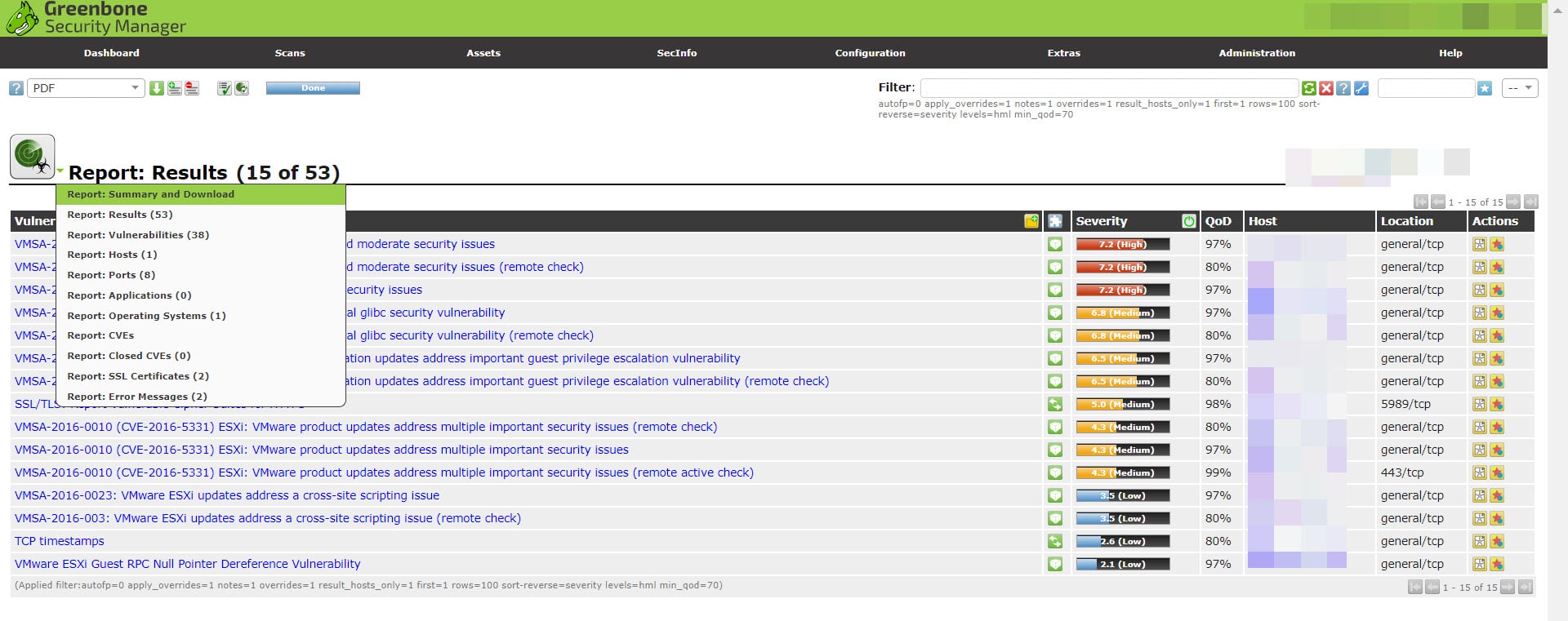
Now, you can find all security issue which discovered on this session of task by click on report number or report date.
Lot of vulnerabilities discovered and because some of those issues are high, immediate action is needed at this situation in production environments.
Next Steps
We’ve reviewed preparation and basic configuration for our Vulnerability Management tools at part 1.
We did scan our ESXi server and find result at part 2.
Next part will be final part and we’ll resolve security issues by applying vendor patches, apply workarounds and hardening guides.
See Also
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 1
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 3