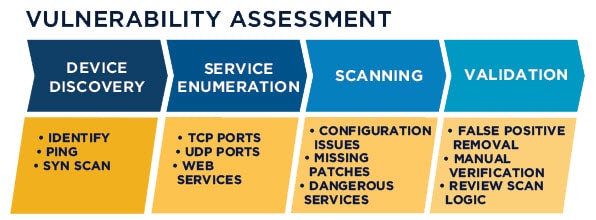
How to Export Big Virtual Machine (>2TB) as OVA or OVF
I guess, you know the instruction but let’s quick review. You can export virtual machines via some different tools such as vSphere Client, vSphere Web Client and others. All administrators do it today and familiar with OVA and OVF. It’s possible to export small virtual machines via vSphere Client, vSphere Web Client, PowerCLI. If you want to export virtual machine with 200~300 GB virtual disks (Thin or Thick), there is serious problem, just make sure that you have enough free space. But did you try to export big or monster VM as OVA or OVF?