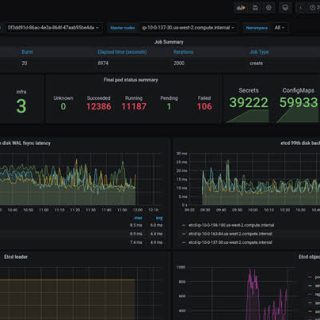
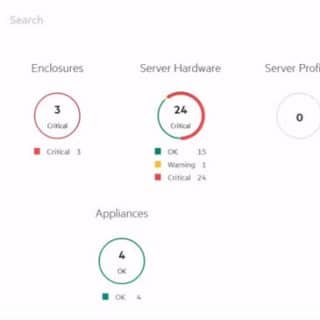
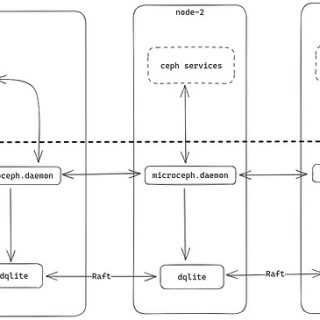
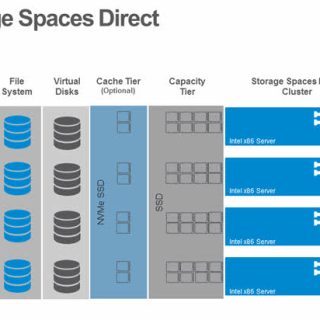
The open-source software defined storage (SDS) colossus, Ceph, has long been praised for its versatility, scalability, and strong feature set. But creating and maintaining a Ceph cluster, especially for small-scale deployments, may be a difficult undertaking best left to storage experts and experienced system administrators. Introducing MicroCeph, an opinionated and streamlined implementation of Ceph that seeks to enable everyone to use this potent storage solution.
Imagine being able to effortlessly manage a fully functional Ceph cluster with only a few finger snaps. That is MicroCeph’s magic. It uses Snaps, a safe and independent Linux packaging standard, to provide a pre-setup, pre-optimized Ceph experience. Forget about laborious orchestration, complicated daemons, and manual configuration; MicroCeph handles everything, from deployment to continuing management.